Internet Browsers DNS over HTTPS
DNS over HTTPS (DoH) and DNS over TLS (DoT)
A new feature to secure your lookups to access websites has started to appear in the most popular browsers. When you type in www.msn.com a DNS server looks up the best address to direct your browser to that website. The transfer of that information is done in the clear and could be seen by someone. DoH and DoT encrypt that request and the result of that request. Although these sites that are doing these lookups for you and providing the result in a encrypted connection, the concern some people have is what these providers/servers will do with that information that is gathered by these requests from your device. Many providers have stated that the requests are not logged, but not all of them have made such a statement about the privacy of this information.
Please note if you are doing a lookup from say Google’s DoH server, and you are looking for www.dell.com the request of the lookup of www.dell.com from that Google DNS server is not secure, but what is passed back to your client is. If you requested of the Google DoH server mail.google.com then the entire request would be private.
Example:
Client Software -encrypted- DoH DNS Server -not encrypted- DNS Root Servers -not encrypted- Specific DNS server for the domain
The information gets cached on the DoH DNS Server you have asked to resolve the name, that lives based on the Time to Live value provided by the DNS Server hosting that domain.
Each browser that provides DoH or DoT are supposed to support a split DNS operation if the DoH server cannot respond or is unable to provide an answer to the request it will fall back to the DNS servers that are provided in the operating system (Windows, Mac, Linux).
If you do not want DoH in your network, and you are a network or server manager that does not want to use DoH or DoT see below for more details. Chromium based browsers are supposed to not enable DNS over HTTPS in a managed environment as the information shows here – https://www.chromium.org/developers/dns-over-https
Firefox will try to enable DoH by prompting the user about the feature as shown below
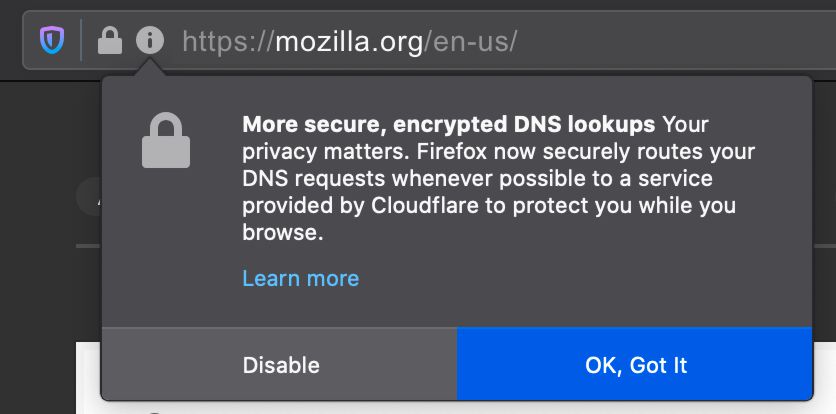
How to Enable DoH in your browser
Chromium browsers like Chrome, New Microsoft Edge, Brave, and Vivaldi have support for DoH in their browsers, not all of them have it enabled by default.
To check Chrome 85 and earlier go to chrome://flags/#dns-over-https
To check Chrome 86 and later click menu in upper right, choose Settings, Privacy and Security, Security, Use secure DNS, default is to use your current DNS if it support DoH, or you can choose from Custom – Cloudflare, CleanBrowsing, or Google.
To check New Microsoft Edge 85 and earlier go to edge://flags/#dns-over-https
To check New Microsoft Edge 86 and later click the menu in the upper right, choose Settings, Privacy, search and services, Security heading, Use secure DNS to specify how to lookup the network address for websites, default is to user your current DNS if it supports DoH, or you can choose Custom – Cloudflare, CleanBrowsing, Google, Quad9.
To check Brave click the menu in the upper right, choose Privacy and security, Security, User secure DNS, With your current service provider if your current DNS supports DoH, or from With you can choose Google, OpenDNS, NextDNS, Cloudflare, Quad9, and CleanBrowsing, also you can choose your own DoH server.
To check Vivaldi go to vivaldi://settings/security, Use secure DNS, With your current service provider if your current DNS support DoH, or With choose your own DoH, Quad9, Cloudflare, OpenDNS, Google, NextDNS, and CleanBrowsing.
After enabling the feature see – https://www.chromium.org/developers/dns-over-https for information on providers that are used, Chromium 83 based browsers and later have the DoH feature, and a set of DoH servers it can use. Setting your DNS server in Windows, Mac, Linux also need to be pointed at a provider that supports DoH.
Firefox has DoH support, in upper right menu, Settings, General, Network Settings, Enable DNS over HTTPS. From this screen you can choose Cloudflare, NextDNS and Other where you provide your own DoH server of choice.
Opera has DoH support, in Settings, Advanced, Enable DNS-over-HTTPS instead of system’s DNS settings. Then you can choose Cloudflare, Google or you provide your own DoH server of choice.
Testing DoH and DoT on your browser
https://www.cloudflare.com/ssl/encrypted-sni/ – Test if your browser is using either DoH or DoT. Look for Secure DNS to show a Green status that browser is using either DoH or DoT.
https://1.1.1.1/help – This site will show if DNS over HTTPS (DoH) or Using DNS over TLS (DoT) are being used by the browser. Site provided by Cloudflare as well.
DoH and DoT in iOS 14.x and iPadOS 14.x and macOS 11.0 and later
For 2020 Apple has added support for DoH and DoT in each iOS, iPadOS and macOS releases. In the case of iOS and iPadOS there are 2 ways this feature can be added.
- A single encrypted DNS server as the default resolver through the use of a network extension app. All applications that need to do DNS lookups would make their request through this app and its settings to make a DoH or DoT.
- Enable encrypted DNS to opt-in directly from the app, this allows that app to make encrypted DoH ot DoT requests even if the rest of the system is not.
The implementation of the DoH and DoT support will be aware of the network it is connected to via Wi-Fi or VPN. It will not override the settings on that network especially if the DoH or DoT requests are not allowed on that network. If the DoH or DoT connection is blocked you should get a prompt on the iPhone or iPad that the encrypted DNS traffic is blocked.
DoH in Windows 11
Go into Settings, Network & Internet, Ethernet and WiFi
Click Edit on the DNS server assignment
Change from Automatic (DHCP) to Manual
Make sure IPv4 is On
Enter a DoH DNS server like 1.1.1.1
and under Preferred DNS encryption choose Encrypted only (DNS over HTTPS)
You can also enter an Alternate DoH server
Click Save
Chrome 85 on Android
Google is rolling out Chrome 85 for Android and is slowly adding the feature to support DoH. In the browser Settings, there will be a new option Secure DNS where you can enable and choose a DoH provider. The browser will have a split DNS feature fallback that will still allow Chrome to use a traditional DNS server. If Android detects that it is on a corporate network it will disable the feature.
DoH Providers
OpenDNS – may not be free for all users
DoH and DoT Management of browsers (Chrome, Firefox, New Microsoft Edge) in business setting
You can through Group Policy turn of the feature of DoH on or off in each Chrome, Firefox and Microsoft Edge.
Chrome policy files – https://chromeenterprise.google/browser/download/ choose Chrome ADM/ADMX Templates to download policy_templates.zip.
- Open Zip file open windows, then admx folders.
- Copy chrome.admx and google.admx to c:\Windows\PolicyDefinitons on the computer you will be updating the GroupPolicy from.
- Then from your language like en-US copy chrome.adml and google.adml into the c:\Windows\PolicyDefinitions\xx-xx where xx-xx is the specific language you need like en-US.
- Now you can edit the policy you want to assign this to change Computer Configuration, Policies, Administrative Templates, Google, Google Chrome, Controls the mode of DNS-over-HTTPS, enabled, choose Disable DNS-over-HTTPS from the menu.
Firefox policy files – https://github.com/mozilla/policy-templates/releases to download policy_templates_v2.2.zip.
- Open Zip file and go into the folder windows.
- Copy firefox.admx and mozilla.admx into c:\Windows\PolicyDefinitions on the computer you will be updating the GroupPolicy from.
- Then from your language like en-US copy firefox.adml and mozilla.adml into the c:\Windows\PolicyDefinitions\xx-xx where xx-xx is the specific language you need like en-US.
- Now you can edit the policy you want to assign this to change Computer Configuration, Policies, Administrative Templates, Mozilla, Firefox, DNS Over HTTPS, Enabled, choose Disable.
New Microsoft Edge – https://www.microsoft.com/en-us/edge/business/download choose version and platform and download the MicrosoftEdgePolicyTemplates.cab.
- Right click the MicrosoftEdgePolicyTemplates.cab and choose Open in new window.
- Open the Zip file go into windows, admx folders.
- Copy msedge.admx and msedgeupdate.admx to c:\Windows\PolicyDefinitions on the computer you will be updating the GroupPolicy from.
- Then from your language like en-US copy msedge.adml and msedgeupdate.adml to c:\Windows\PolicyDefinitions\xx-xx where xx-xx is the specific language you need like en-US.
- Now you can edit the policy you want to assign this to change Computer Configuration, Policies, Administrative Templates, Microsoft Edge, Control the mode of DNS-over-HTTPS, enabled, choose Disable DNS-over-HTTPS from the menu.
